Alla företag bör engagera sig i betalningssäkerhet. År 2024 rapporterade 79 % av organisationerna att de var måltavlor för betalningsbedrägeri. Och betalningsbedrägerier kan vara otroligt dyra, med ett genomsnittligt dataintrång som globalt kostar 4,4 miljoner USD. Företag måste prioritera betalningssäkerhet för att skydda sina kunders känsliga information, upprätthålla kundernas förtroende och undvika kostsamma ekonomiska förluster.
Den här guiden innehåller praktiska steg för att utveckla och implementera en robust strategi för betalningssäkerhet. Oavsett om du är en detaljhandlare inom e-handel, en fysisk butik eller en SaaS-leverantör beror framgången för din företag delvis på en stark betalningssäkerhetsstrategi.
Vad innehåller den här artikeln?
- Vad är betalningssäkerhet?
- Principer för betalningssäkerhet
- Säkerhetsfunktioner att leta efter hos en betalleverantör
- Bästa säkerhetspraxis för företag
- Hur Stripe Radar kan hjälpa till
Vad är betalningssäkerhet?
Betalningssäkerhet avser de system, processer och åtgärder som skyddar finansiella transaktioner från obehörig åtkomst, dataintrång och bedrägerier. För både onlineföretag och fysiska företag är det viktigt att säkerställa betalningssäkerheten för att upprätthålla kundernas förtroende, minimera ekonomiska förluster och följa relevanta regler och branschstandarder.
Principer för betalningssäkerhet
Det finns flera principer för betalning som samverkar för att skydda finansiella transaktioner och kunddata. De viktigaste att känna till inkluderar:
Kryptering
Kryptering skyddar känsliga kunddata och finansiella transaktioner från obehörig åtkomst, manipulering och stöld. Det finns två primära typer av kryptering: symmetrisk och asymmetrisk. Symmetrisk kryptering innebär att man använder samma nyckel för att låsa och låsa upp data, medan asymmetrisk kryptering, även känd som "kryptering med offentlig nyckel", använder två nycklar: en offentlig nyckel för låsning och en privat nyckel för att låsa upp data. I allmänhet anses asymmetrisk kryptering vara säkrare eftersom den privata nyckeln inte delas.
Företag använder krypteringsprotokoll som Secure Sockets Layer (SSL) och Transport Layer Security (TLS) för att säkra dataöverföring mellan kunders webbläsare och företagens webbplatser eller betalningsplattformar. SSL/TLS-kryptering använder en kombination av symmetrisk och asymmetrisk kryptering för att upprätta en säker anslutning och skydda data under överföringen.
Tokenisering
Tokenisering skyddar känslig betalningsinformation genom att ersätta den med unika token som inte har något egenvärde om de komprometteras. Den här processen minskar risken för obehörig åtkomst och dataintrång avsevärt och upprätthåller efterlevnad av branschstandarder och föreskrifter.
Betalningstokenisering ersätter känsliga uppgifter, såsom kreditkortsnummer, med unika tokens som genereras av ett säkert system. Dessa tokens används för att referera till den ursprungliga betalningsinformationen, som lagras i ett centraliserat tokenvalv. Tokens i sig kan inte användas för att utföra bedrägliga transaktioner, och de kan heller inte bakåtkompileras för att avslöja de ursprungliga betalningsuppgifterna.
Autentisering
Autentisering är en grundläggande betalningssäkerhetsåtgärd som verifierar användare som försöker få åtkomst till eller slutföra en transaktion.
Det finns flera typer av autentisering, bland annat:
- Enfaktorsautentisering (SFA): Kräver någon form av identifiering, vanligtvis ett lösenord eller en PIN-kod
- Tvåfaktorsautentisering (2FA): Kräver två typer av identifiering, till exempel ett lösenord och en engångskod som skickas till en registrerad enhet
- Multifaktorautentisering (MFA): Kräver tre eller fler former av identifiering, vilket kan inkludera biometriska data, säkerhetsfrågor eller fysiska tokens
Identifiering och förebyggande av bedrägerier
Dessa system hjälper företag att identifiera och förhindra bedrägliga transaktioner genom att övervaka transaktionsmönster, kundbeteenden och andra riskfaktorer. Tekniker som maskininlärningsalgoritmer, beteendeanalys och riskvärdering kan upptäcka avvikelser och förhindra bedrägeri. För mer information, se vårbedrägeridetekteringsguide.
Efterlevnad av betalkortbranschens standarder för datasäkerhet
Payment Card Industry Data Security Standard (PCI DSS) är en uppsättning säkerhetsstandarder som är utformade för att säkerställa att alla företag som behandlar, lagrar eller överför kreditkortsinformation upprätthåller en säker miljö.PCI DSS-efterlevnad skyddar känsliga kunddata och minimerar risken för dataintrång.
Att uppnå och upprätthålla PCI DSS-efterlevnad är viktigt för att skydda kundernas känsliga betalningar och visa engagemang för säkerhet.
Betalningsgateways
Betalningsportaler underlättar behandlingen av korttransaktioner samtidigt som kundbetalningsdata skyddas från obehörig åtkomst och bedrägeri. Genom att tillhandahålla en säker kanal för överföring av betalningsinformation mellan kunden, företaget ochbetalleverantören ellerförvärvande bank är betalningsportaler en viktig komponent i en mycket säker betalningsmiljö.
Brandvägg och nätverkssäkerhet
Brandvägg och nätverkssäkerhet hjälper till att skydda betalningsinfrastruktur och konfidentiella kunddata från externa hot som hackare, skadlig kod och andra bedrägliga aktörer.
En brandvägg är en typ av säkerhetssystem som fungerar som en säkerhetsvakt för ett datornätverk. Den kontrollerar informationen som kommer in och skickas ut baserat på specifika regler. Brandväggar skapar en barriär mellan ett betrott nätverk inom ett företag, till exempel betalningssystemet, och den opålitliga omvärlden, till exempel internet, vilket bidrar till att förhindra obehörig åtkomst till nätverket. Brandväggar kan vara maskinvarubaserade, programvarubaserade eller en kombination av båda.
Några viktiga aspekter av brandväggs- och nätverkssäkerhet är:
Nätverkssegmentering
Att dela upp nätverket i mindre, isolerade segment hjälper till att begränsa potentiella skador av ett säkerhetsintrång. Genom att hålla känsliga betalningsdata och system i separata nätverkssegment kan företag skydda dessa tillgångar från obehörig åtkomst och möjliggöra PCI DSS-efterlevnad.System för upptäckt och förebyggande av intrång (IDPS)
IDPS-lösningar övervakar nätverkstrafik för att upptäcka misstänkt aktivitet, identifierar potentiella hot och vidtar åtgärder för att förhindra eller minimera dessa hot. Genom att använda en kombination av metoder, som att söka efter kända hot och analysera kommunikationsregler, kan IDPS-lösningar identifiera och blockera många typer av attacker, även de som är helt nya.Starka åtkomstkontroller
Åtkomstkontroller som multifaktorautentisering (MFA), rollbaserad åtkomstkontroll och "principen om lägsta behörighet" – metoden att ge individer eller enheter den lägsta åtkomstnivå som krävs för att de ska kunna utföra sina specifika uppgifter eller funktioner relaterade till betalningshantering – säkerställer att endast behöriga användare kan komma åt nätverksresurser och känsliga betalningssystem.Säkerhetsövervakning och incidenthantering
Kontinuerlig övervakning av nätverksaktivitet, i kombination med en väldefinierad incidenthanteringsplan, hjälper företag att snabbt identifiera och agera på säkerhetshot, vilket minimerar potentiella skador och driftstopp.
Säkerhetsuppdateringar och korrigeringar
Programvaruleverantörer, maskinvarutillverkare och operativsystemleverantörer släpper säkerhetsuppdateringar och korrigeringar för att åtgärda kända sårbarheter, buggar eller andra säkerhetsproblem i sina produkter. Regelbundna säkerhetsuppdateringar och patchar hjälper till att skydda betalningsinfrastruktur, kunddata och andra viktiga system från sårbarheter, cyberattacker och obehörig åtkomst.
Genom att tillämpa dessa uppdateringar och korrigeringar regelbundet kan du:
Åtgärda sårbarheter
Uppdateringar och korrigeringar åtgärdar säkerhetsbrister eller svagheter som hackare kan utnyttja för att få obehörig åtkomst till dina system eller stjäla känsliga data. Genom att hålla dig uppdaterad med säkerhetsuppdateringar kan du minska risken för dataintrång och cyberattacker.Förbättra prestanda
Uppdateringar innehåller ofta prestandaförbättringar, buggfixar eller nya funktioner som kan förbättra den övergripande stabiliteten, effektiviteten och funktionaliteten i dina system och din programvara.Säkerställa efterlevnad
Regelkrav dikterar ofta att företag tillämpar säkerhetsuppdateringar och korrigeringar i tid för att upprätthålla efterlevnad. Att uppdatera dina system regelbundet kan hjälpa dig att undvika böter eller påföljder i samband med bristande efterlevnad.Skydda sig mot nya hot
Cyberhoten fortsätter att utvecklas i takt med att hackare upptäcker nya sårbarheter och utvecklar nya attacktekniker. Genom att tillämpa uppdateringar och korrigeringar kan du ligga steget före dessa nya hot och upprätthålla en säker miljö.
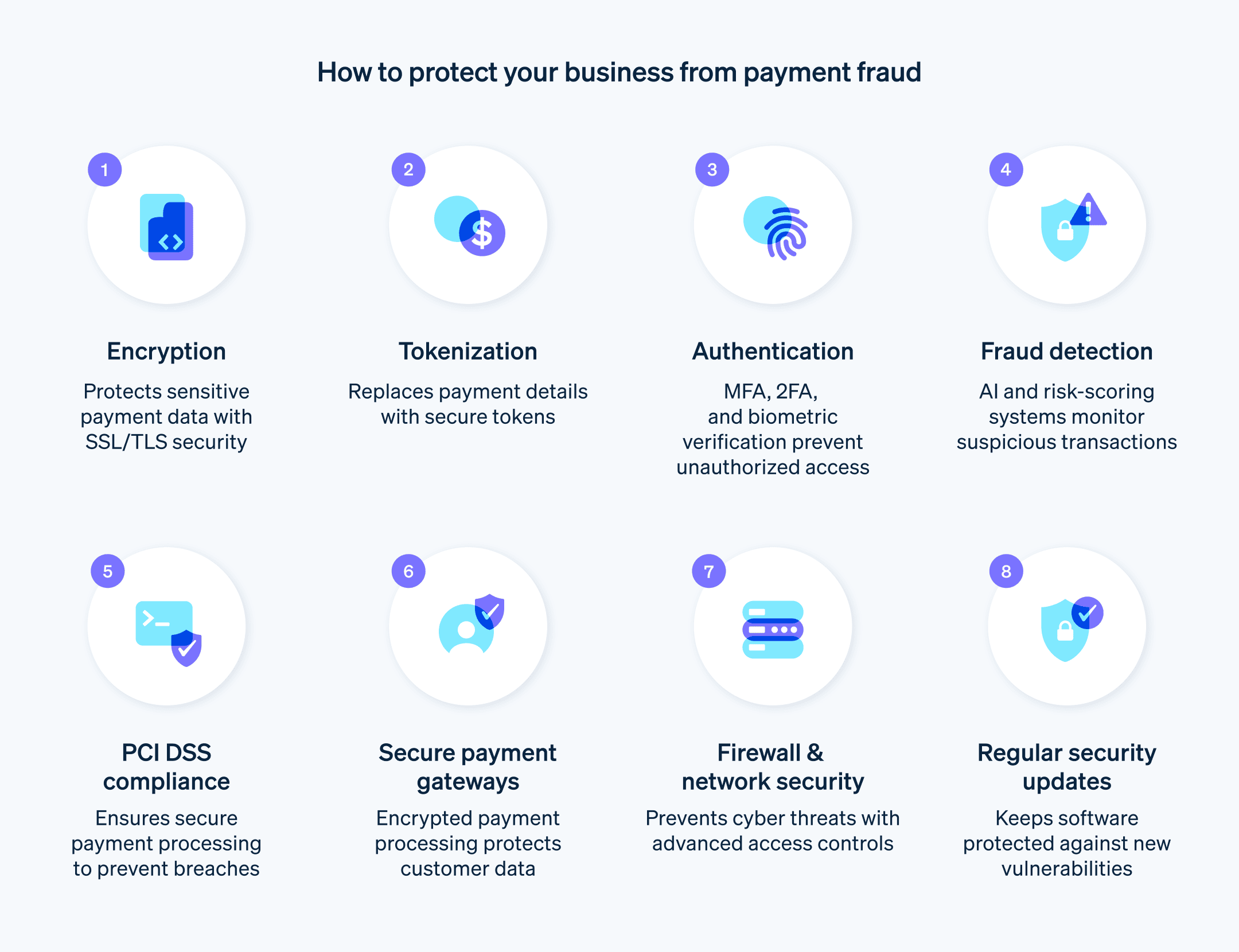
Säkerhetsfunktioner att leta efter hos en betalleverantör
När du väljer en betalningsleverantör finns det mycket att tänka på – från säkerhetsfunktioner till efterlevnad, upptid och tillförlitlighet.
Viktiga funktioner att leta efter hos en betalningsleverantör är bland annat:
Kryptering
En leverantör av säkra betalningar bör använda krypteringsprotokoll för att kryptera känsliga betalningar. Dessa protokoll säkerställer att kundens betalningar förblir säkra under överföringen, vilket skyddar data från avlyssning eller manipulering.Tokenisering
Betalningsdata som kortinformation bör tokeniseras för att skydda kunddata, minska risken för dataintrång och behålla PCI DSS-efterlevnaden.Autentisering och förebyggande av bedrägerier
Inbyggda autentiseringsmetoder, såsom CVV/CVC-kod-kontroller,3D Secure och biometrisk autentisering för att verifiera kundidentitet och förhindra obehöriga transaktioner. Se dessutom till att de använder system för avancerad upptäckt och förebyggande av bedrägerier som använder maskininlärning, beteendeanalys och riskbedömning för att identifiera och blockera bedrägliga transaktioner i realtid.Efterlevnad av branschstandarder
En leverantör bör följa PCI DSS och andra relevanta branschstandarder för att upprätthålla en säker miljö för behandling, lagring och överföring av kortinnehavardata.Drifttid och tillförlitlighet
Att upprätthålla hög upptid och tillförlitlighet säkerställer att kunderna kan slutföra transaktioner utan avbrott. Regelbunden övervakning, redundansåtgärder och robust infrastruktur gör det möjligt för en leverantör att konsekvent behandla transaktioner på ett säkert och effektivt sätt.
Bästa säkerhetspraxis för företag
Alla företag som behandlar, lagrar eller överför betalningsinformation, inklusive kreditkortsdata, måste bry sig om betalningssäkerhet. Att upprätthålla säkra betalningar är viktigt för att skydda känsliga kunddata, säkerställa kundernas förtroende och följa branschstandarder och regler – för företag av alla storlekar och i alla branscher.
För att säkerställa en genomtänkt strategisk plan för att hantera betalningssäkerhet bör företag vidta följande steg:
1. Gör en riskbedömning
Börja med att titta på din nuvarande betalningsinfrastruktur, dina processer och dina system för att identifiera potentiella sårbarheter och förbättringsområden. Utvärdera vilka typer av känsliga data ditt företag hanterar och var de lagras, bearbetas och överförs.
2. Förstå efterlevnadskraven
Bekanta dig med de standarder och föreskrifter som styr din bransch, inklusive PCI DSS, och avgör ditt företags specifika efterlevnadskrav baserat på de marknader där du är verksam. Se till att du förstår de säkerhetskontroller och metoder som krävs av dessa standarder. Utbilda dina anställda i PCI DSS-krav och bästa praxis för att hantera kortinnehavardata på ett säkert sätt.
3. Utveckla säkerhetspolicyer och säkerhetsrutiner
Upprätta tydliga policyer och procedurer som hanterar betalningssäkerhet, inklusive riktlinjer för hantering av känsliga data, åtkomstkontroller, incidenthantering, säkerhetsuppdatering och utbildning av anställda. Se till att dessa policyer och procedurer överensstämmer med branschens standarder och föreskrifter.
4. Vidta säkerhetsåtgärder
Baserat på dina riskbedömnings- och efterlevnadskrav implementerar du lämpliga säkerhetsåtgärder, till exempel kryptering, tokenisering, stark autentisering och brandväggskonfigurationer. Välj en säker betalningsleverantör och arbeta med PCI DSS-kompatibla leverantörer för att effektivisera efterlevnaden.
5. Övervaka system och utför stresstester
Övervaka regelbundet dina betalningar, nätverk och applikationer för potentiella hot eller sårbarheter. Taktiker som sårbarhetsskanningar, penetrationstester och systemrevisioner kan bedöma effektiviteten av dina säkerhetsåtgärder och identifiera områden som kan förbättras. Överväg dessutom att använda automatiserade verktyg som kan hjälpa till att identifiera saknade säkerhetsuppdateringar eller föråldrad programvara.
6. Justera ditt tillvägagångssätt
Även de bästa säkerhetsstrategierna kommer att behöva justeras och anpassas med tiden. Utvärdera kontinuerligt hur pass effektiv din strategi för betalningssäkerhet är och justera den vid behov för att hantera förändringar i verksamheten, branschen eller hotbilden. Regelbundna granskningar säkerställer att din strategi förblir relevant och effektiv när det gäller att skydda dina kunders data.
7. Skapa en incidenthanteringsplan
Utveckla en väldefinierad incidenthanteringsplan för att vägleda din organisation i händelse av ett dataintrång eller en annan incident. Denna plan bör beskriva roller och ansvarsområden, kommunikationsprotokoll och förfaranden för att begränsa och mildra incidenten.
Hur Stripe Radar kan hjälpa till
Stripe Radar tränar AI-modeller att upptäcka och förhindra bedrägeri, med hjälp av data från det globala Stripe-nätverket. Det uppdaterar kontinuerligt dessa modeller baserat på de senaste bedrägerierna, vilket skyddar ditt företag när bedrägerierna utvecklas.
Stripe erbjuder även Radar for Fraud Teams, som gör det möjligt för användare att lägga till anpassade regler som hanterar bedrägeriscenarier för just deras företag och få tillgång till avancerade bedrägeriinsikter.
Radar kan hjälpa ditt företag att:
- Förhindra bedrägeriförluster: Stripe hanterar över 1 biljon dollar i betalningar årligen. Denna omfattning gör det möjligt för Radar att på ett korrekt sätt upptäcka och förhindra bedrägerier, vilket sparar pengar.
- Öka intäkterna: Radars AI-modeller är tränade på verkliga tvistdata, kundinformation, webbläsardata etc. Detta gör att Radar kan identifiera riskabla transaktioner och minska falska positiva resultat, vilket ökar dina intäkter.
- Spara tid: Radar är inbyggt i Stripe och kan konfigureras med noll kodrader. Du kan också övervaka din bedrägeriprestanda, skriva regler och annat på en enda plattform, vilket ökar effektiviteten.
Innehållet i den här artikeln är endast avsett för allmän information och utbildningsändamål och ska inte tolkas som juridisk eller skatterelaterad rådgivning. Stripe garanterar inte att informationen i artikeln är korrekt, fullständig, adekvat eller aktuell. Du bör söka råd från en kompetent advokat eller revisor som är licensierad att praktisera i din jurisdiktion för råd om din specifika situation.