Product
Supporting additional payment methods for agentic commerce

Stripe is now the first and only provider that supports both agentic network tokens and buy now, pay later tokens in agentic commerce through a single primitive.

Stripe is now the first and only provider that supports both agentic network tokens and buy now, pay later tokens in agentic commerce through a single primitive.

State-of-the-art LLMs can now solve a majority of scoped coding problems, but it’s an open question whether they can fully autonomously manage software engineering projects. We spent months building evaluation environments to benchmark how well AI agents can create real Stripe integrations.

Together, Metronome and Stripe are building the most flexible and complete billing solution on the market—one that works for everyone, from engineers in a garage figuring out their business model to public companies monetizing at global scale.

Not only are the majority of retailers actively implementing, or have plans to implement, agentic commerce, but many are also moving to a more tactical phase of optimizing their setup—refining their product catalog strategy to launch faster and investing in their own agentic shopping experiences in addition to integrating with third-party agents.
Gain next-day access to cash, and use funds where they’re needed most. Get reliable auto-settlement in a few clicks right from the Dashboard.
Businesses in Australia can now offer PayTo. Accept one-off and recurring direct debits with PayTo to get real-time payment confirmation and funds deposited into your Stripe balance instantly, 24 hours a day, every day of the year.
Tempo, a Layer 1 blockchain incubated by Stripe and crypto VC firm Paradigm, is purpose-built for scalable, low-cost stablecoin payments.
Give customers in France the option to pay with Alma, so they can choose to complete their purchase in two, three, or four installments—while you get paid immediately.
Businesses in the UK can now offer Pay by Bank. Accept payments in real time, and reduce payment costs with Stripe’s open banking–powered payment method.
Manual payouts will now land in your bank account on the same business day due to new local banking integrations in the UK. No extra fees, no integrations changes needed.
Businesses in the US can now offer Amazon Pay. Allow your customers to pay using the same checkout experience that millions of Amazon customers know and trust.
Businesses in the US can now reach new customers with Cash App Pay. Allow customers to pay with the wallet that's number one in both app stores.
Build custom experiences for interactions from ordering to loyalty management—or run your custom POS on an all-in-one device.
Businesses can now accept more buy now, pay later methods globally through one integration on Stripe: Klarna in AU, NZ, CA, CH, PT, PL, CZ, and GR; Affirm in CA.

2025 was a breakout year for early-stage startups, as founders launched more companies and generated revenue faster than ever. Three shifts stand out: customer bases are more international than ever, time-to-revenue has compressed, and founders are turning their attention to AI agents over AI infrastructure or copilots.

In a new study, we found a strong causal relationship between accepting financing and growing revenue on Stripe. Learn which businesses are most likely to benefit, and how greater access to financing could drive significant GDP growth.

Today, we’re introducing the Agentic Commerce Suite: a new solution that gets your business agent-ready. It enables you to sell on AI agents more easily by making your products discoverable, simplifying your checkout, and allowing you to accept agentic payments via a single integration.

Leading SaaS platforms across industries—from Squarespace to Jobber—are using embedded components to ship payments and finance features with minimal code. We analyzed the data to see which types of platforms are getting the most value.

We recently launched three new features that give you more control to fine-tune your risk and compliance strategy, allowing you to use more of Stripe’s data to inform your approach. Here’s what’s new.

We recently released a series of improvements to expand multiprocessor support, give you more control over your billing and invoicing models, and better tailor your pricing for AI products. Here’s everything that’s new.

Join us May 6–8 in San Francisco for Stripe Sessions, our annual user conference. This year, we’re doubling the number of breakout sessions, expanding our training program to give you more hands-on product support, and adding a demo stage to showcase more of Stripe’s key updates.

We announced AI-powered payments, our biggest-ever upgrades to Stripe Connect, new support for usage-based billing, increased interoperability, and a lot more.

Please join us April 23–25 at Moscone West in San Francisco for our largest event ever.
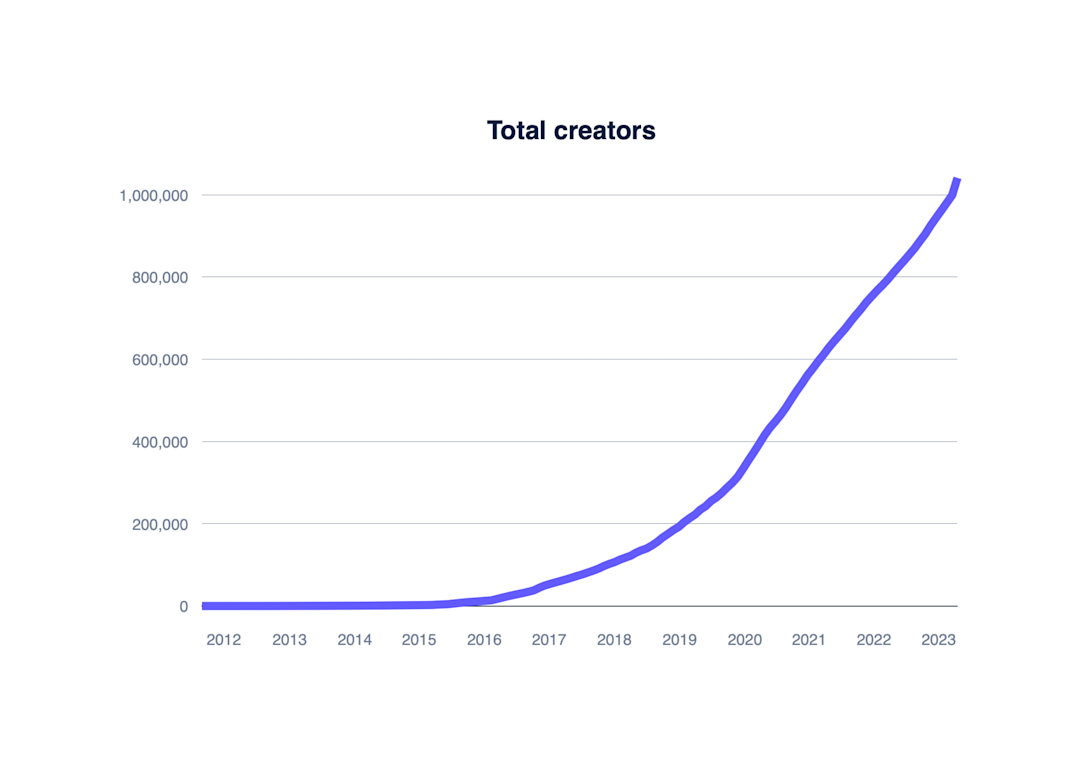
Stripe data shows that the creator economy has evolved but is still thriving. We’ve seen this evolution up close, as many of the largest creator platforms use Stripe Connect to onboard creators and pay out funds around the world.

At our annual user conference, we shared how we are helping businesses increase revenue with our global payments suite, how we are allowing platforms and marketplaces to generate more revenue and get to market faster, and how we are helping businesses find new efficiencies through developer tools and automated revenue and finance operations.

State-of-the-art LLMs can now solve a majority of scoped coding problems, but it’s an open question whether they can fully autonomously manage software engineering projects. We spent months building evaluation environments to benchmark how well AI agents can create real Stripe integrations.

Among global business leaders surveyed, 84% agree that adapting pricing quickly will be a key competitive advantage. Our new real-time analytics system for Stripe Billing helps them spot customer trends just as they emerge.
Stripe’s users rely on us to calculate tax correctly and quickly, no matter where a transaction happens. Our new jurisdiction resolution system (JRS) is a faster, less resource-intensive solution to the challenging problem of determining tax obligations in places with complicated, overlapping tax jurisdictions.
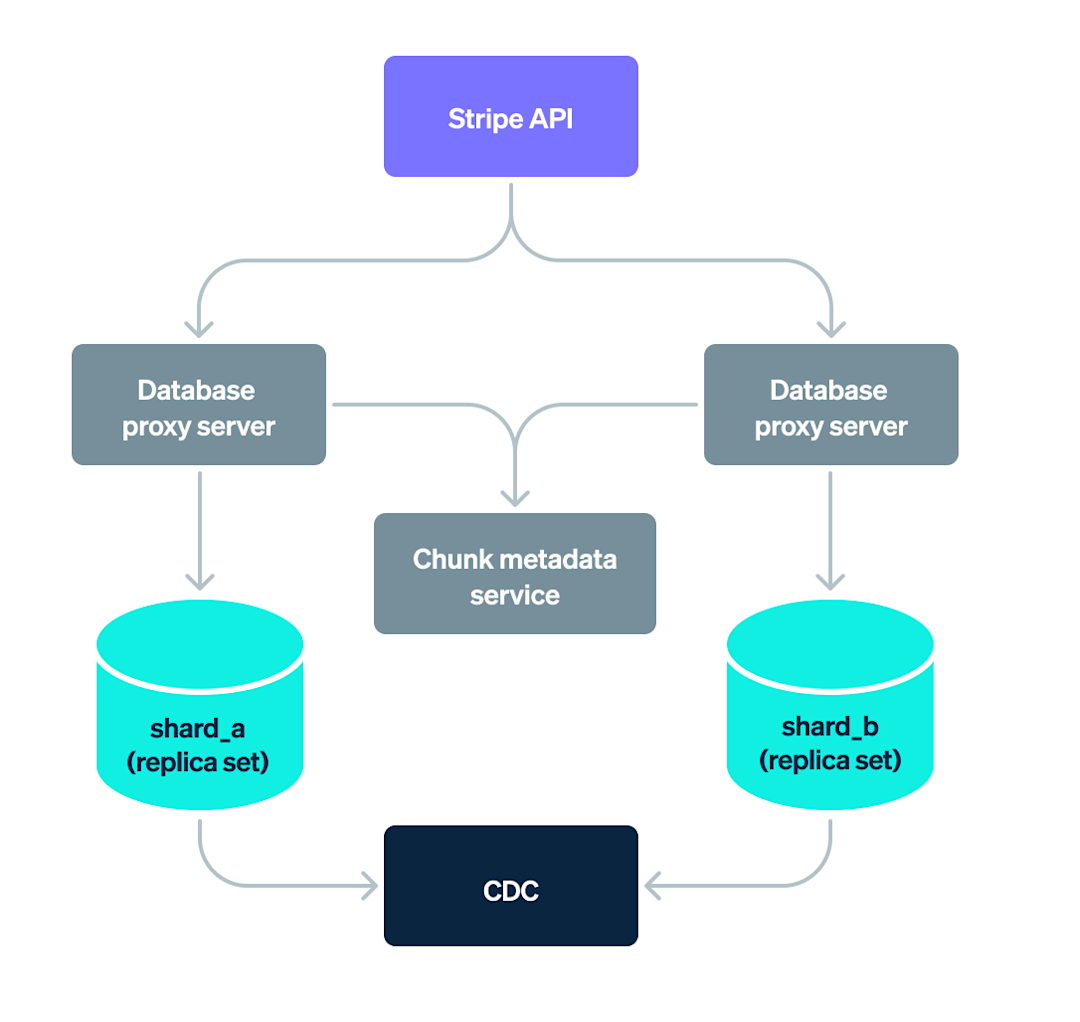
In this blog post we’ll share an overview of Stripe’s database infrastructure and discuss the design and application of the Data Movement Platform.

Stripe Billing allows businesses to manage customer relationships with recurring payments, usage triggers, and other customizable features.

Not only are the majority of retailers actively implementing, or have plans to implement, agentic commerce, but many are also moving to a more tactical phase of optimizing their setup—refining their product catalog strategy to launch faster and investing in their own agentic shopping experiences in addition to integrating with third-party agents.
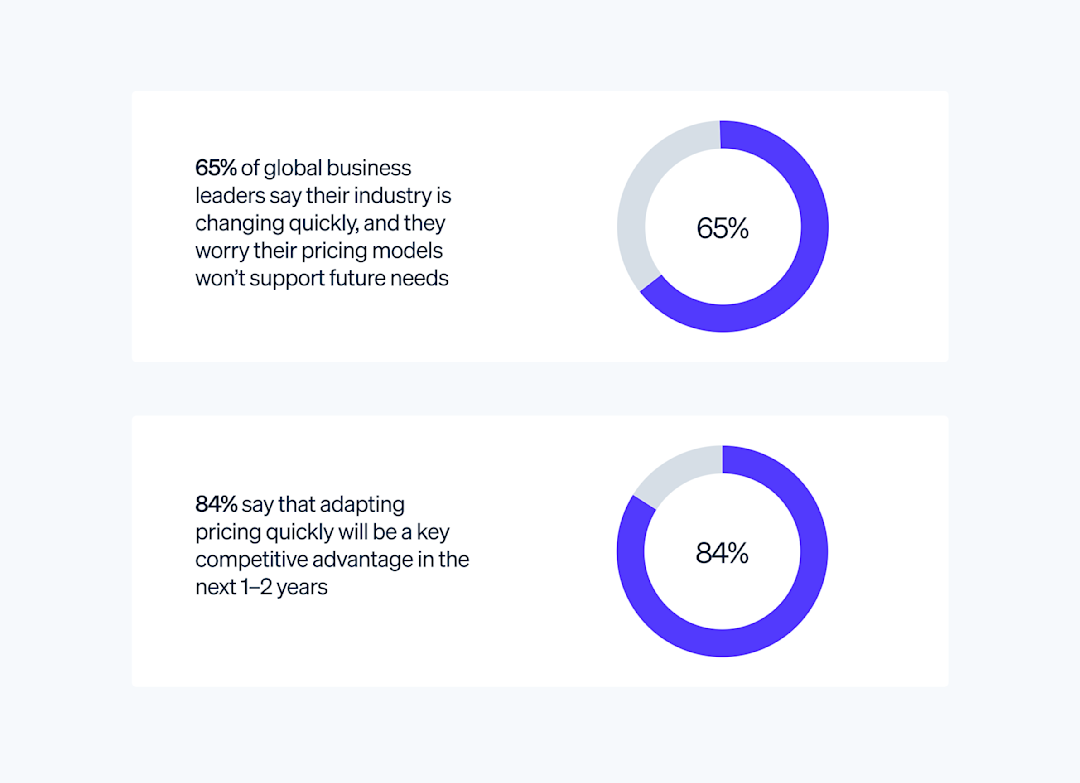
Our recent survey of 2,000+ global business leaders showed that the fastest-growing companies are approaching pricing differently than their peers. Here are some of the strategies behind their success.
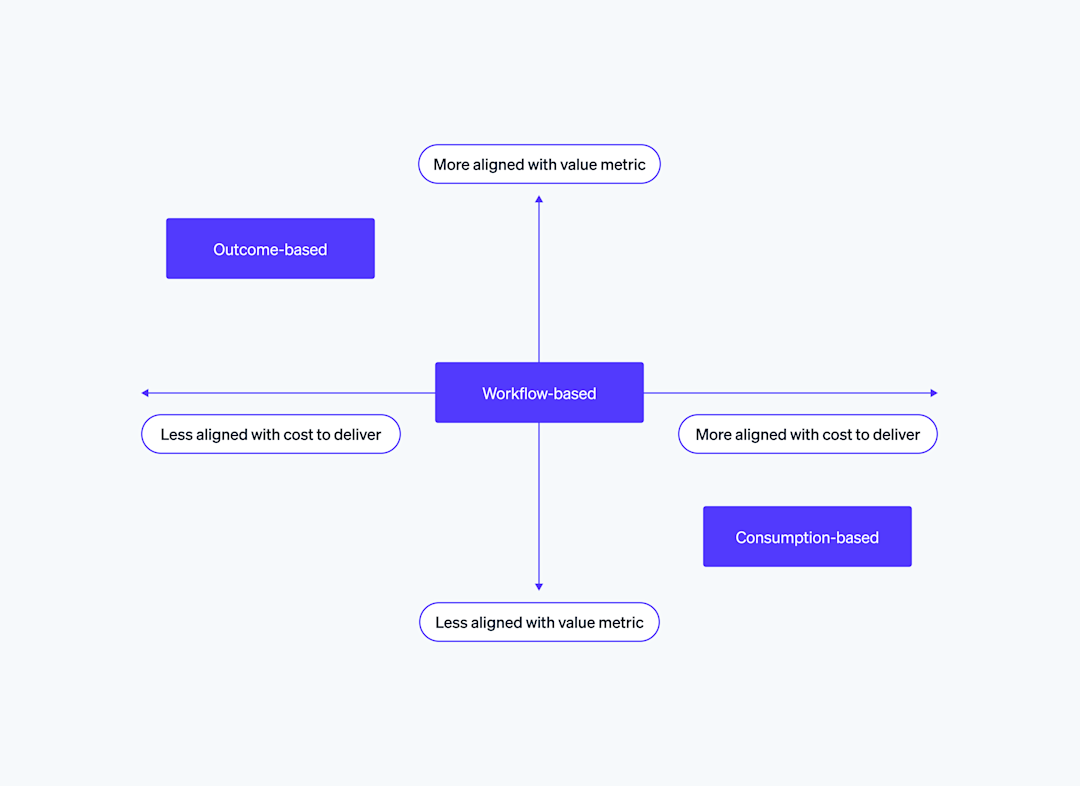
While businesses are rapidly building AI products, monetization remains a challenge. In this post, we share a framework for building a successful pricing strategy with key decision points on charge metrics, billing models, and guardrails.
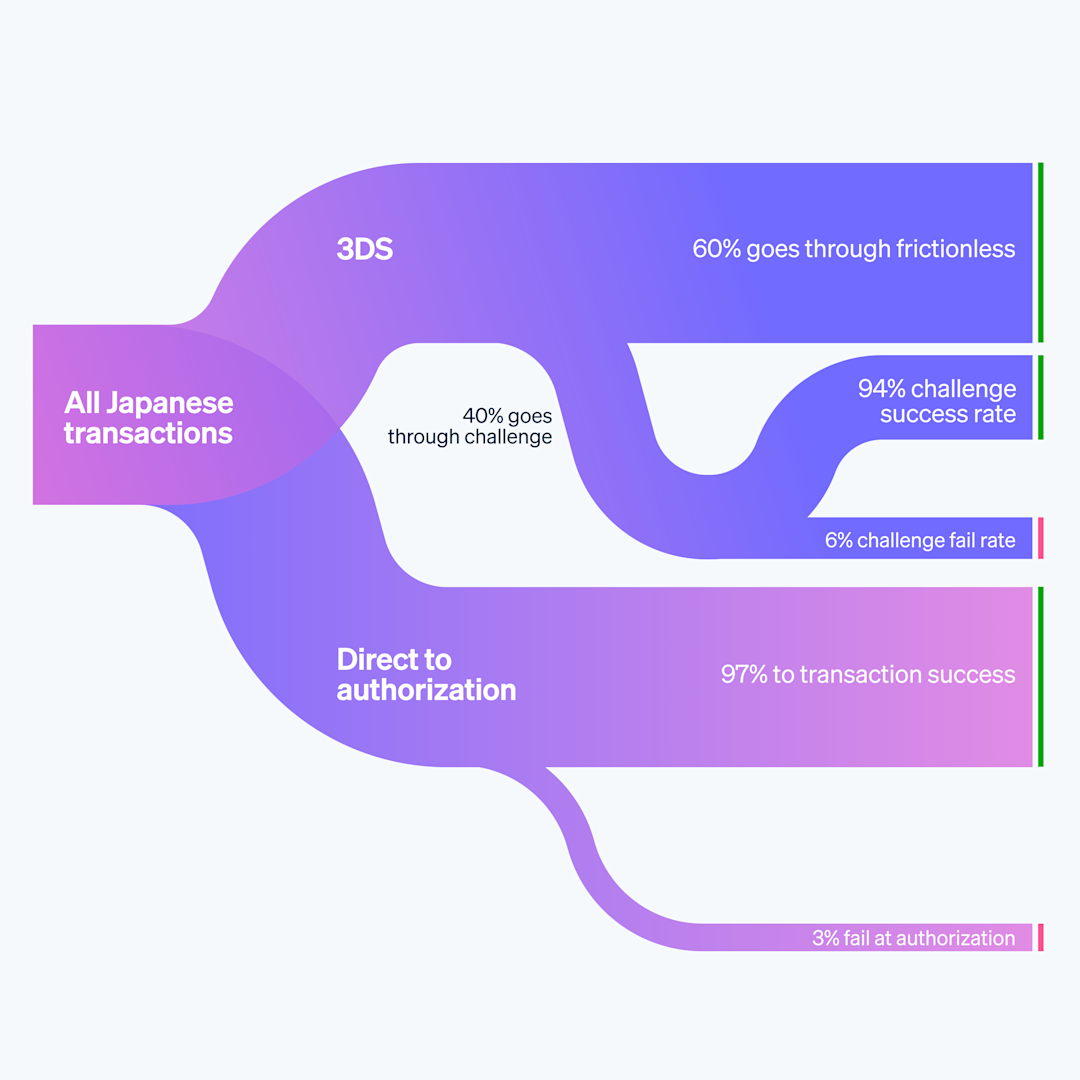
Our analysis showed that even with very high two-factor authentication trigger rates—which traditionally add friction to the checkout flow—France, the UK, and Japan still maintain high conversion rates.
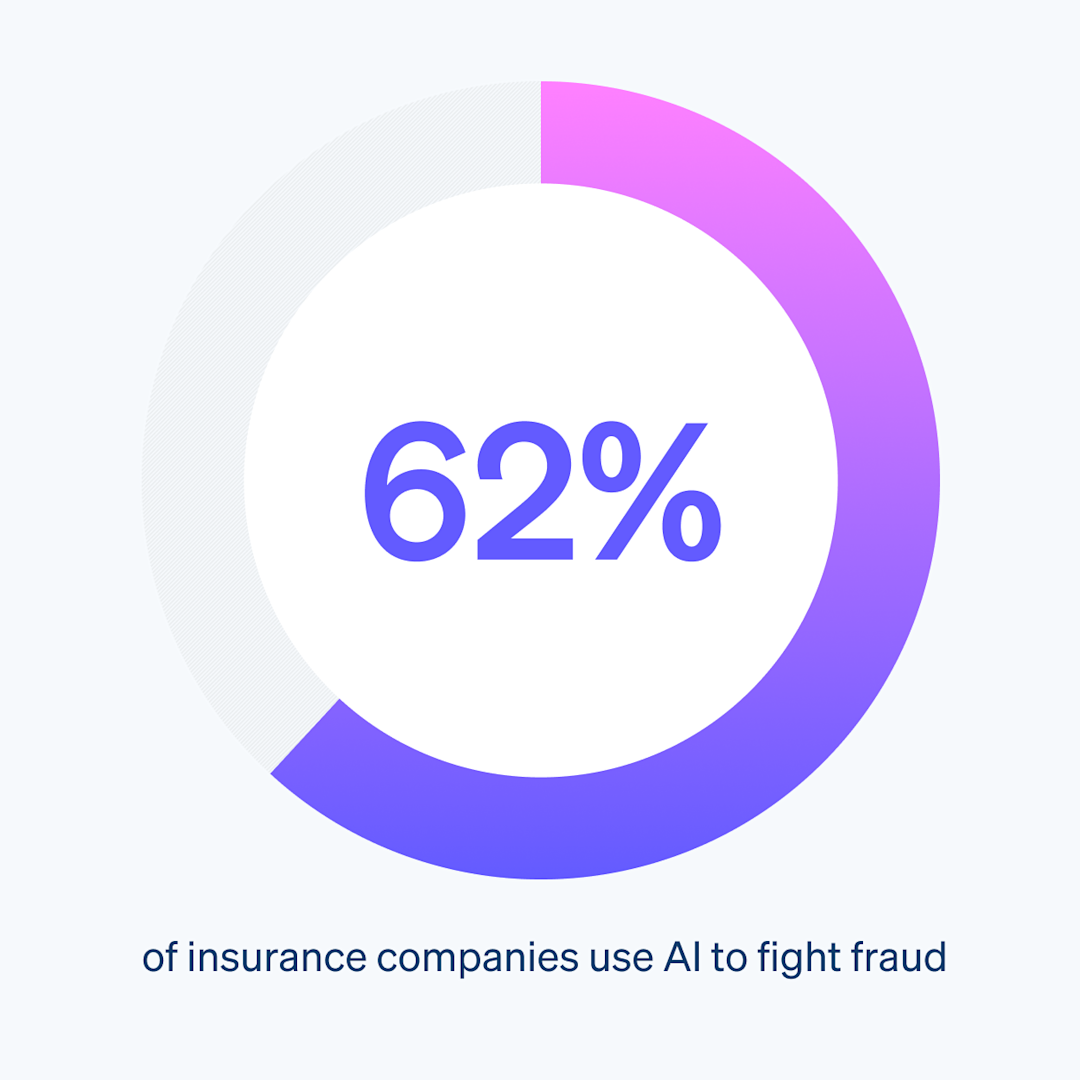
Our recent survey of more than 4,000 payments leaders worldwide showed that 47% of businesses now use an AI tool or feature to detect and prevent fraud—making it the most popular application of AI in payments. But adoption isn’t uniform across all sectors. Understanding which types of companies are leading this shift—and why—offers insights into where fraud prevention is heading and which strategies are most effective.

Together, Metronome and Stripe are building the most flexible and complete billing solution on the market—one that works for everyone, from engineers in a garage figuring out their business model to public companies monetizing at global scale.

2025 was a breakout year for early-stage startups, as founders launched more companies and generated revenue faster than ever. Three shifts stand out: customer bases are more international than ever, time-to-revenue has compressed, and founders are turning their attention to AI agents over AI infrastructure or copilots.

In a new study, we found a strong causal relationship between accepting financing and growing revenue on Stripe. Learn which businesses are most likely to benefit, and how greater access to financing could drive significant GDP growth.

Today, we’re introducing the Agentic Commerce Suite: a new solution that gets your business agent-ready. It enables you to sell on AI agents more easily by making your products discoverable, simplifying your checkout, and allowing you to accept agentic payments via a single integration.

Leading SaaS platforms across industries—from Squarespace to Jobber—are using embedded components to ship payments and finance features with minimal code. We analyzed the data to see which types of platforms are getting the most value.