Storing customer credit card information is a requirement for nearly all businesses, but finding the best way to do so isn’t always straightforward. Specific requirements and regulations are in place regarding card storage, and businesses must maintain compliance without sacrificing the customer experience or their own operational efficiency. Credit card fraud is a serious and prevalent issue: in the United States, for example, 65% of credit card holders have been victims of fraud. For businesses, safe storage of customer card data is an important safeguard against fraud.
Below, we’ll cover the Payment Card Industry Data Security Standard (PCI DSS), the primary security standard governing customer card storage, and outline best practices that businesses can adopt for storing customer credit card information safely and efficiently.
What’s in this article?
- How does card storage work?
- What is the PCI DSS?
- PCI requirements for card storage
- Best practices for card storage
- Card storage challenges and solutions
- How Stripe can help
How does card storage work?
Card storage refers to businesses’ retaining customer payment card information, including credit and debit card numbers and associated identifying details. The four categories of data that businesses typically store are the cardholder name, primary account number (PAN), expiration date, and service code.
Businesses can choose from a variety of systems for card storage, and these typically involve components such as dedicated data storage systems, encryption and tokenization techniques, and data loss prevention (DLP) tools.
What is the PCI DSS?
The PCI DSS is a set of security standards that govern how businesses should accept, process, store, and transmit credit card information. This standard protects cardholder data from fraud and theft, and any organization that handles credit card transactions must adhere to it. The PCI DSS is managed by the Payment Card Industry Security Standards Council, which was founded by major credit card companies such as Visa, Mastercard, American Express, Discover, and JCB. Complying with PCI DSS helps businesses reduce the risk of data breaches and ensure their card transactions are secure.
PCI requirements for card storage
The PCI DSS details requirements for businesses regarding card storage, such as:
Limit data storage: Store only cardholder data that is necessary for business needs. Do not store sensitive authentication data after authorization, even if encrypted. This includes data such as the full magnetic stripe, card validation code, or personal identification number (PIN)/PIN block.
Protect stored data: Encrypt all stored cardholder data including the PAN, which should be rendered unreadable anywhere it is stored using methods such as cryptography.
Limit data access: Access to cardholder data should be limited to individuals whose jobs require such access. Implement a need-to-know policy that restricts access.
Create unique IDs: Assign a unique ID to each person with computer access to cardholder data. After a data breach, this helps track who accessed data.
Protect physical locations: Protect the physical locations where cardholder data is stored. This includes measures such as surveillance, restricted access to data storage areas, and secure storage systems.
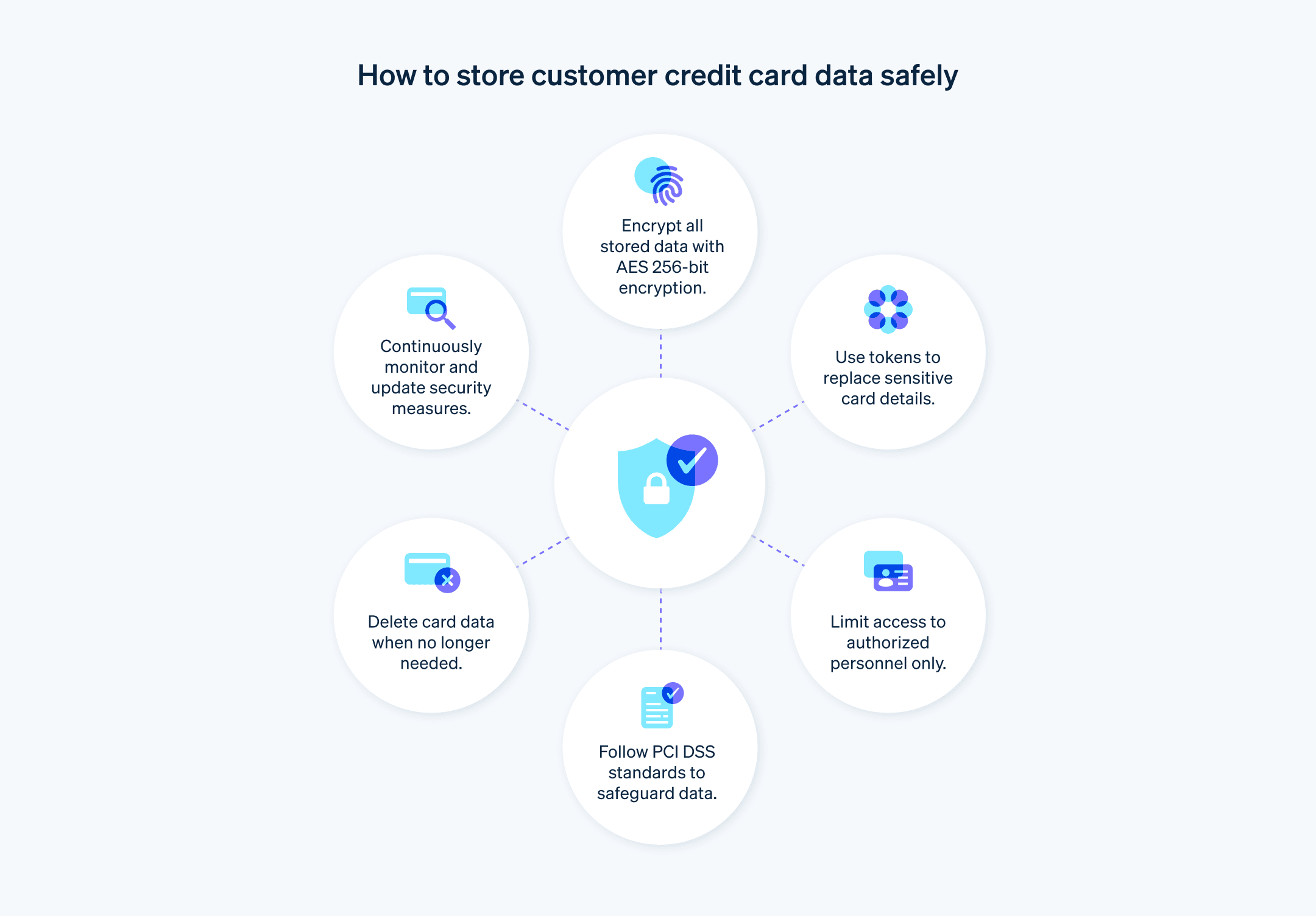
Set retention and disposal policies: Develop a data retention policy that deletes cardholder data as soon as it’s no longer required. Delete that type of data, and ensure it is unrecoverable.
Use encryption keys: Manage and implement the use of strong cryptography and security protocols such as Secure Sockets Layer (SSL)/Transport Layer Security (TLS) or Internet Protocol Security (IPSEC) to safeguard sensitive cardholder data during transmission over open, public networks.
Best practices for card storage
Businesses can take many routes to adhere to PCI compliance requirements. These best practices will help businesses protect their customers’ card information and maintain PCI compliance in a way that protects the user experience:
Minimize cardholder data storage: Store only required cardholder information, and avoid retaining sensitive data unless absolutely necessary. Reducing the amount of stored data can minimize risk and simplify compliance efforts.
Adopt advanced encryption standard (AES): Use AES with a 256-bit key for encrypting stored cardholder data. This methodology aligns with current best practices and surpasses minimum compliance requirements.
Implement end-to-end encryption (E2EE): Beyond basic encryption practices, deploy E2EE to safeguard cardholder data from the point of capture until it reaches the secure processing environment.
Improve access control mechanisms: Use multifactor authentication and granular role-based access controls to ensure only authorized personnel can access sensitive cardholder data, with a clear audit trail for all access and actions taken.
Integrate DLP tools: Implement DLP strategies to monitor and control data transfer, preventing unauthorized data exfiltration and ensuring cardholder data is not improperly stored or distributed.
Conduct regular security tests: To proactively identify and remediate potential security weaknesses, conduct sophisticated penetration testing and vulnerability assessments beyond the standard PCI DSS requirements.
Consider advanced tokenization techniques: Consider using dynamic tokenization, in which tokens vary with each transaction, to provide an additional layer of security and further reduce the usefulness of intercepted data.
Employ automated compliance monitoring: Use automated tools to continuously monitor compliance with PCI DSS standards and promptly detect and address any deviations.
Use a zero-trust architecture: Adopt a zero-trust security framework that assumes all users, even those within the organization, could potentially compromise cardholder data, enforcing strict verification and minimal access principles.
Explore quantum-resistant cryptography tools: To protect against emerging threats posed by quantum computing, explore the integration of quantum-resistant cryptographic algorithms.
Develop a response plan: Have a plan for responding to security incidents. If a data breach occurs, you should be able to quickly identify the issue, contain the breach, and mitigate any potential damage.
Card storage challenges and solutions
Card storage is closely tied to many aspects of the customer experience, how products and services are accessed, and how the internal team manages its engagement with customer data. Even the most well-designed card storage systems will create a considerable amount of complexity. Here are a few common challenges along with solutions:
Scalability
- Challenge: As transaction volumes grow, it can be difficult to maintain high performance and PCI compliance. Scalability issues have the potential to affect customer experience and operational efficiency.
- Solution: Implement distributed database architectures that can handle high read/write throughputs while maintaining data consistency and compliance. Use elastic cloud-based solutions that can scale dynamically in response to fluctuating demand, maintaining performance without compromising security.
Legacy system integration
- Challenge: Many organizations use legacy systems that are not designed to meet PCI DSS standards. This can create compliance and security gaps.
- Solution: Use data abstraction layers or service-oriented architectures to encapsulate legacy systems, minimizing direct access to cardholder data. Consider replacing or modernizing legacy systems over time using microservices or containerization to improve agility and compliance.
Data privacy across borders
- Challenge: Different regions have different data protection regulations, and compliance requirements increase for businesses when they store cardholder data across borders.
- Solution: Implement data residency solutions that process and store data in compliance with local regulations. Use geolocation-based data storage and processing to automatically route and store data according to the cardholder’s location and in adherence to regional compliance requirements.
Advanced security threats
- Challenge: Because attackers are continually evolving tactics, organizations must fight against increasingly sophisticated cyberattacks and advanced persistent threats (APTs) that can bypass conventional security measures.
- Solution: Adopt a layered security approach that includes advanced threat detection and response mechanisms such as AI-driven behavioral analytics to identify and mitigate threats in real time. Regularly update incident response and disaster recovery plans to address new types of cyberthreats.
Evolving compliance standards
- Challenge: PCI DSS standards and related regulatory requirements are continually evolving, and staying compliant can be an ongoing challenge.
- Solution: Establish a continuous compliance monitoring program that uses automated compliance tracking and reporting tools. Engage in proactive industry forums and collaborations to stay ahead of emerging standards and incorporate best practices into your compliance strategy.
Data quality and consistency
- Challenge: It can be difficult to ensure the integrity and consistency of cardholder data across a variety of systems and storage environments, especially in distributed architectures.
- Solution: Implement strong data governance frameworks, and use data quality management tools that maintain data accuracy and consistency. Use data synchronization and replication techniques that adhere to atomicity, consistency, isolation, and durability (ACID) properties to maintain data integrity.
How Stripe can help
Working with Stripe can help businesses reduce the burden of PCI DSS compliance. By processing payments through Stripe, businesses do not handle sensitive card data directly, which reduces the scope of their compliance responsibilities. Stripe is a certified PCI Service Provider Level 1, the highest level of PCI compliance, and handles the majority of card data security tasks. These Stripe features keep cardholder data safe while helping businesses stay PCI compliant:
Tokenization: Stripe’s tokenization service replaces sensitive card details with unique identifiers (tokens), which can be safely stored and used for transactions without exposing card details.
E2EE: Stripe encrypts all sensitive data from the point of capture until it is processed within its secure environment. This end-to-end encryption minimizes the risk that data will be intercepted during transmission.
Scalability: Stripe’s infrastructure is built on a cloud platform designed to handle large volumes of transactions without compromising performance. Businesses can scale their operations without worrying about maintaining compliance and security standards.
Integration with modern and legacy systems: Stripe offers extensive application programming interface (API) support, which makes it easy to integrate with modern and legacy systems. This flexibility helps businesses modernize their payment processing without the need for extensive overhauls of existing systems.
Continuous monitoring and updates: Stripe continuously monitors its systems for threats and regularly updates its security measures to tackle emerging vulnerabilities. Security features include machine learning algorithms that detect and prevent fraud.
Global compliance: Stripe operates globally and can help businesses deal with the complexities of data residency and regional compliance across borders.
Data governance: Stripe’s infrastructure supports data integrity and consistency.
By relying on Stripe to manage most of the responsibility regarding secure card storage, data encryption, compliance, and scalability, businesses can spend more time on core operations. Learn more about Stripe’s security standards.
The content in this article is for general information and education purposes only and should not be construed as legal or tax advice. Stripe does not warrant or guarantee the accurateness, completeness, adequacy, or currency of the information in the article. You should seek the advice of a competent attorney or accountant licensed to practice in your jurisdiction for advice on your particular situation.