Armazenar informações de cartão de crédito do cliente é um requisito para quase todas as empresas, mas encontrar a melhor maneira de fazer isso nem sempre é simples. Há requisitos e regulamentos específicos para o armazenamento de cartões, e as empresas devem manter a conformidade sem sacrificar a experiência do cliente ou sua própria eficiência operacional. As fraudes com cartões de crédito são um problema sério e comum: nos Estados Unidos, por exemplo, 65% dos titulares de cartões de crédito foram vítimas de fraude. Para as empresas, o armazenamento seguro dos dados dos cartões dos clientes é uma proteção importante contra fraudes.
Explicamos o Padrão de Segurança de Dados do Setor de Cartões de Pagamento (PCI DSS), o principal padrão de segurança que rege o armazenamento de cartões de clientes, e descrevemos as práticas recomendadas para armazenar informações de cartões de crédito de clientes com segurança e eficiência.
Neste artigo:
- Como funciona o armazenamento de cartões?
- O que é o PCI DSS?
- Requisitos de PCI para armazenamento de cartões
- Práticas recomendadas para armazenamento de cartões
- Desafios e soluções para armazenamento de cartões
- Como a Stripe pode ajudar
Como funciona o armazenamento de cartões?
O armazenamento de cartões é a retenção de dados de cartões de pagamento dos clientes, incluindo números de cartões de crédito e débito e dados de identificação associados. As quatro categorias de dados que as empresas normalmente armazenam são o nome do titular do cartão, o número principal da conta (PAN), a data de validade e o código do serviço.
As empresas podem escolher diversos sistemas para armazenamento de cartões, normalmente com componentes como sistemas dedicados de armazenamento de dados, criptografia e tokenização e ferramentas de prevenção de perda de dados (DLP).
O que é o PCI DSS?
O PCI DSS é um conjunto de padrões de segurança que regem como as empresas devem aceitar, processar, armazenar e transmitir dados de cartões de crédito. Esta norma protege os dados de titulares de cartão de fraudes e roubos, e qualquer organização que lida com transações com cartão de crédito deve aderir. O PCI DSS é gerenciado pelo Payment Card Industry Security Standards Council, fundado pelas principais empresas de cartões de crédito, como Visa, Mastercard, American Express, Discover e JCB. A conformidade com o PCI DSS ajuda as empresas a reduzir o risco de violações de dados e garantir a segurança.
Requisitos de PCI para armazenamento de cartões
O PCI DSS detalha os requisitos para empresas em relação ao armazenamento de cartões, como:
Limitar o armazenamento de dados: armazene apenas os dados de titulares de cartão necessários para o trabalho da empresa. Não armazene dados de autenticação confidenciais após a autorização, mesmo que criptografados. Isso inclui dados como a tarja magnética completa, código de validação do cartão ou número de identificação pessoal (PIN)/bloco de PIN.
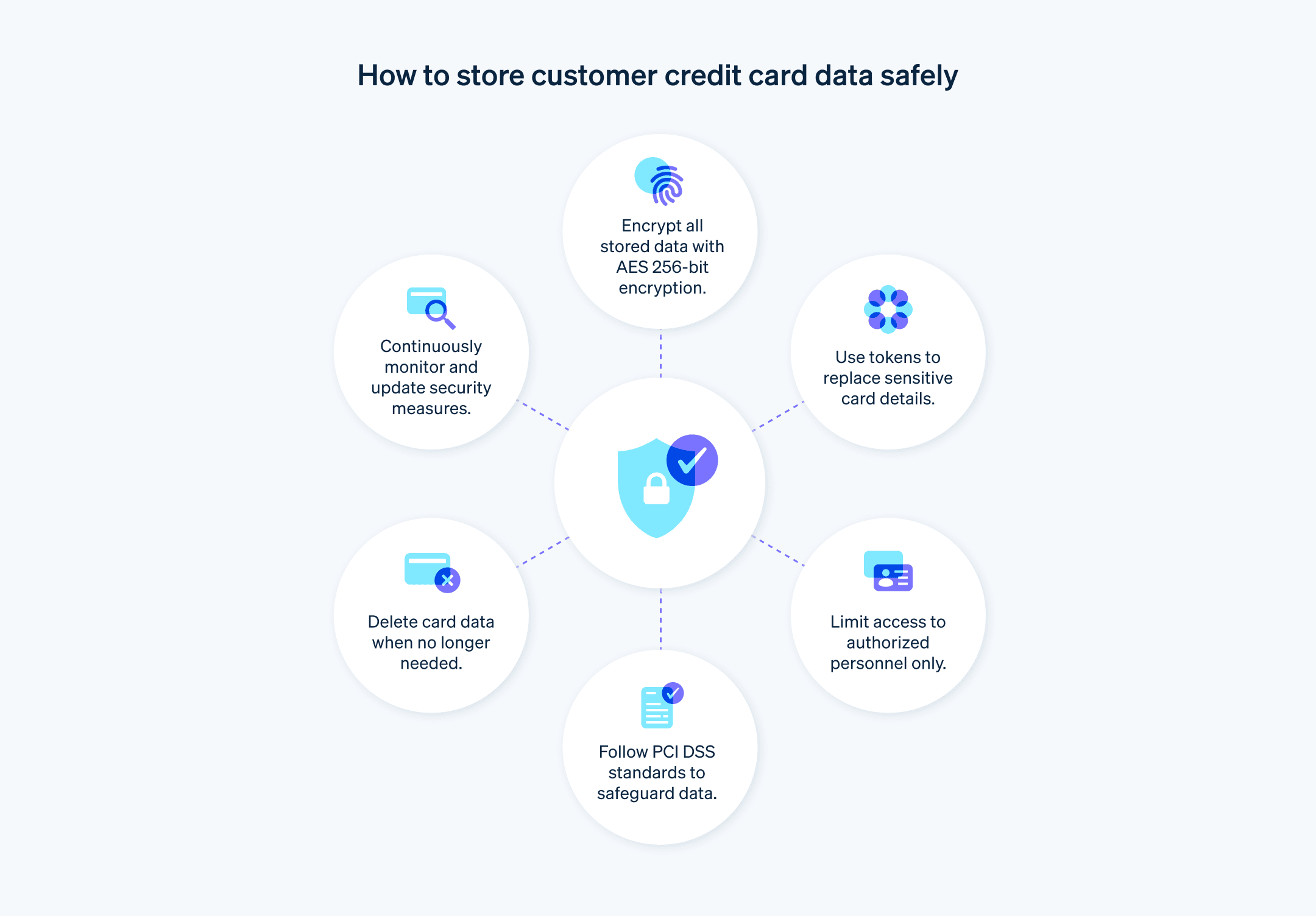
Proteger os dados armazenados: criptografe todos os dados armazenados do titular do cartão, incluindo o PAN, que deve ser ilegível em qualquer lugar de armazenamento, com métodos como criptografia.
Limitar o acesso aos dados: o acesso aos dados de titulares de cartão deverá limitar-se a indivíduos cujas funções exijam esse acesso. Implemente uma política de necessidade de conhecimento que restrinja o acesso.
Criar IDs exclusivos: atribua um ID único a cada pessoa com acesso aos dados de titulares. Após uma violação de dados, isso ajuda a rastrear quem acessou os dados.
Proteger locais físicos: proteja os locais físicos onde os dados de titulares de cartão são armazenados. Isso inclui medidas como vigilância, acesso restrito a áreas de armazenamento de dados e sistemas de armazenamento seguros.
Definir políticas de retenção e descarte: desenvolva uma política de retenção de dados que exclua os dados dos titulares de cartão assim que eles não forem mais necessários. Exclua esse tipo de dados e certifique-se de que eles sejam irrecuperáveis.
Usar chaves de criptografia: gerencie e implemente criptografia forte e protocolos de segurança, como SSL (Secure Sockets Layer)/TLS (Transport Layer Security) ou IPSEC, para proteger dados confidenciais do titular do cartão durante a transmissão em redes públicas abertas.
Práticas recomendadas para armazenamento de cartões
As empresas podem adotar várias medidas para aderir aos requisitos de conformidade PCI. Essas práticas recomendadas ajudam a proteger os dados dos cartões dos clientes e manter a conformidade com PCI de forma a proteger a experiência do usuário:
Minimize o armazenamento de dados de titulares de cartão: armazene apenas as informações necessárias e evite reter dados confidenciais, exceto se for absolutamente necessário. Reduzir a quantidade de dados armazenados pode minimizar os riscos e simplificar a conformidade.
Adote o padrão avançado de criptografia (AES): use AES com uma chave de 256 bits para criptografar dados armazenados do titular do cartão. Essa metodologia está alinhada às melhores práticas atuais e supera os requisitos mínimos de conformidade.
Implemente criptografia de ponta a ponta (E2EE): além das práticas básicas de criptografia, implante E2EE para proteger os dados de titulares de cartão desde o ponto de captura até que eles atinjam o ambiente de processamento seguro.
Melhore os mecanismos de controle de acesso: use autenticação multifator e controles de acesso específicos por função para garantir que somente pessoas autorizadas possam acessar dados sigilosos de titulares de cartão, com uma trilha de auditoria clara para todos os acessos e ações realizadas.
Integre ferramentas DLP: implemente estratégias de DLP para monitorar e controlar a transferência de dados, evitando a exfiltração não autorizada de dados e garantindo que os dados de titulares de cartão não sejam armazenados ou distribuídos indevidamente.
Realize testes de segurança regulares: para identificar e remediar proativamente possíveis falhas de segurança, realize testes de penetração sofisticados e avaliações de vulnerabilidade além dos requisitos padrão do PCI DSS.
Considere técnicas avançadas de tokenização: considere o uso de tokenização dinâmica, na qual os tokens variam com cada transação, para aumentar a segurança e reduzir ainda mais a utilidade dos dados interceptados.
Empregue monitoramento automatizado de conformidade: use ferramentas automatizadas para monitorar continuamente a conformidade com os padrões PCI DSS e detectar e resolver prontamente os desvios.
Use uma arquitetura de confiança zero: adote uma estrutura de segurança de confiança zero que pressupõe que todos os usuários, mesmo aqueles dentro da organização, podem comprometer os dados de titulares de cartão, impondo verificação rigorosa e princípios de acesso mínimo.
Explore ferramentas de criptografia resistentes ao quântico: para se proteger contra novas ameaças representadas pela computação quântica, explore a integração de algoritmos criptográficos resistentes ao quântico.
Crie um plano de resposta: tenha um plano para incidentes de segurança. Se ocorrer uma violação de dados, é preciso identificar rapidamente o problema, conter a violação e mitigar qualquer dano.
Desafios e soluções para armazenamento de cartões
O armazenamento de cartões está intimamente ligado a muitos aspectos da experiência do cliente, como os produtos e serviços são acessados e como a equipe interna gerencia seu envolvimento com os dados do cliente. Mesmo os sistemas mais bem projetados têm uma quantidade considerável de complexidade. Astão alguns desafios comuns e soluções:
Escalabilidade
- Desafio: com o aumento do volume de transações, pode ser difícil manter o alto desempenho e a conformidade com PCI. Problemas de escalabilidade têm o potencial de afetar a experiência do cliente e a eficiência operacional.
- Solução: implemente arquiteturas de banco de dados distribuídas que possam lidar com altas taxas de transferência de leitura/gravação enquanto mantêm a consistência e a conformidade dos dados. Use soluções elásticas em nuvem que podem ser dimensionadas em resposta à demanda flutuante, mantendo o desempenho sem comprometer a segurança.
Integração de sistemas obsoletos
- Desafio: muitas organizações usam sistemas obsoletos que não foram projetados para atender aos padrões PCI DSS. Isso pode criar lacunas de conformidade e segurança.
- Solução: use camadas de abstração de dados ou arquiteturas orientadas a serviços para encapsular sistemas antigos, minimizando o acesso direto aos dados de titulares de cartão. Considere substituir ou modernizar esses sistemas com o tempo usando microsserviços ou conteinerização para melhorar a agilidade e a conformidade.
Privacidade de dados internacional
- Desafio: regiões diferentes têm regulamentos de proteção de dados diferentes, e os requisitos de conformidade aumentam para as empresas quando armazenam dados de titulares de cartão internacionalmente.
- Solução: implemente soluções de residência de dados que processam e armazenam dados em conformidade com as regulamentações locais. Use o armazenamento e o processamento de dados baseados em geolocalização para encaminhar e armazenar dados automaticamente de acordo com a localização do titular e em conformidade com os requisitos regionais de conformidade.
Ameaças avançadas à segurança
- Desafio: como os atacantes desenvolvem sempre novas táticas, as organizações precisam combater ataques cibernéticos cada vez mais sofisticados e ameaças persistentes avançadas (APTs) que podem contornar as medidas de segurança convencionais.
- Solução: adote uma abordagem de segurança em camadas que inclua mecanismos avançados de detecção e resposta a ameaças, como análises comportamentais orientadas por IA, para identificar e mitigar ameaças em tempo real. Atualize regularmente os planos de resposta a incidentes e de recuperação de desastres para lidar com novos tipos de ameaças cibernéticas.
Evolução dos padrões de conformidade
- Desafio: as normas PCI DSS e os requisitos normativos correspondentes evoluem continuamente, e manter a conformidade é um desafio constante.
- Solução: estabeleça um programa contínuo de monitoramento de conformidade que use ferramentas automatizadas de rastreamento e relatórios de conformidade. Participe de fóruns e colaborações proativas do setor para ficar à frente dos padrões emergentes e incorporar as melhores práticas em sua estratégia de conformidade.
Qualidade e uniformização dos dados
- Desafio: pode ser difícil garantir a integridade e a consistência dos dados de titulares de cartão em diversos sistemas e ambientes de armazenamento, especialmente em arquiteturas distribuídas.
- Solução: implemente estruturas sólidas de governança de dados e use ferramentas de gerenciamento de qualidade de dados que mantenham a precisão e a consistência dos dados. Use técnicas de sincronização e replicação de dados, que adotam propriedades de atomicidade, uniformidade, isolamento e durabilidade (ACID) para manter a integridade dos dados.
Como a Stripe pode ajudar
O trabalho com Stripe pode ajudar as empresas a reduzir a sobrecarga da conformidade com o PCI DSS. Ao processar pagamentos na Stripe, as empresas não gerencia diretamente os dados sigilosos de cartões, o que reduz o escopo de suas responsabilidades de conformidade. A Stripe é um provedor de serviços PCI certificado nível 1, o mais alto nível de conformidade com PCI, e gerencia a maioria das tarefas de segurança de dados de cartão. Esses recursos da Stripe protegem os dados de titulares de cartão e ajudam a manter a conformidade com PCI:
Tokenização: o serviço de tokenização da Stripe substitui dados sigilosos de cartão por identificadores exclusivos (tokens), que podem ser armazenados e usados com segurança em transações sem exposição de dados do cartão.
E2EE: a Stripe criptografa todos os dados confidenciais desde o ponto de captura até que sejam processados em seu ambiente seguro. Essa criptografia de ponta a ponta minimiza o risco de que os dados sejam interceptados durante a transmissão.
Escalabilidade: a infraestrutura da Stripe é construída em uma plataforma em nuvem projetada para lidar com grandes volumes de transações sem comprometer o desempenho. As empresas podem escalar suas operações sem se preocupar com a manutenção dos padrões de conformidade e segurança.
Integração com sistemas modernos e legados: a Stripe oferece amplo suporte à interface de programação de aplicativos (API), o que facilita a integração com sistemas modernos e obsoletos. Essa flexibilidade ajuda as empresas a modernizar seu processamento de pagamentos, sem a necessidade de revisões extensas dos sistemas existentes.
Monitoramento e atualizações contínuas: a Stripe monitora continuamente seus sistemas em busca de ameaças e atualiza regularmente suas medidas de segurança para lidar com vulnerabilidades emergentes. Os recursos de segurança incluem machine learning algoritmos que detectam e evitam fraudes.
Conformidade global: a Stripe opera globalmente e pode ajudar empresas a gerenciar as complexidades da residência de dados e da conformidade regional.
Governança de dados: a infraestrutura da Stripe oferece suporte à integridade e consistência dos dados.
Usando a Stripe para gerenciar a maior parte da responsabilidade em relação ao armazenamento seguro de cartões, criptografia de dados, conformidade e escalabilidade, as empresas podem gastar mais tempo nas operações principais. Saiba mais sobre os padrões de segurança da Stripe.
O conteúdo deste artigo é apenas para fins gerais de informação e educação e não deve ser interpretado como aconselhamento jurídico ou tributário. A Stripe não garante a exatidão, integridade, adequação ou atualidade das informações contidas no artigo. Você deve procurar a ajuda de um advogado competente ou contador licenciado para atuar em sua jurisdição para aconselhamento sobre sua situação particular.