Att lagra kunders kreditkortsuppgifter är ett krav för nästan alla företag, men att hitta det bästa sättet att göra det är inte alltid enkelt. Det finns specifika krav och regler för lagring av kortuppgifter, och företag måste upprätthålla efterlevnad utan att det påverkar kundupplevelsen eller den operativa effektiviteten. Kreditkortsbedrägerier är ett allvarligt och utbrett problem: i USA har till exempel 65 % av kreditkortsinnehavarna fallit offer för bedrägeri. För företag är säker lagring av kunders kortuppgifter ett viktigt skydd mot bedrägerier.
Nedan tar vi upp Payment Card Industry Data Security Standard (PCI DSS), den primära säkerhetsstandarden som styr lagring av kunders kortuppgifter, och beskriver bästa praxis som företag kan använda för att lagra kundernas kreditkortsuppgifter på ett säkert och effektivt sätt.
Vad innehåller den här artikeln?
- Hur fungerar lagring av kortuppgifter?
- Vad är PCI DSS?
- PCI-krav för lagring av kortuppgifter
- Bästa praxis för lagring av kortuppgifter
- Utmaningar och lösningar för lagring av kortuppgifter
- Så här kan Stripe hjälpa dig
Hur fungerar lagring av kortuppgifter?
Lagring av kortuppgifter innebär att företag behåller kundernas betalkortsuppgifter, inklusive kredit- och bankkortsnummer och tillhörande identifieringsuppgifter. De fyra kategorier av data som företag vanligtvis lagrar är kortinnehavarens namn, kontonummer, kortets utgångsdatum och tjänstkod.
Företag kan välja mellan en mängd olika system för kortlagring, och dessa involverar vanligtvis komponenter som dedikerade datalagringssystem, krypteringstekniker och tokeniseringstekniker samt verktyg för att förhindra dataförlust (DLP).
Vad är PCI DSS?
PCI DSS är en uppsättning säkerhetsstandarder som styr hur företag ska ta emot, behandla, lagra och överföra kreditkortsuppgifter. Denna standard skyddar kortinnehavarens data från bedrägeri och stöld, och alla organisationer som hanterar kreditkortstransaktioner måste följa den. PCI DSS förvaltas av Payment Card Industry Security Standards Council, som grundades av stora kreditkortsföretag som Visa, Mastercard, American Express, Discover och JCB. Att följa PCI DSS hjälper företag att minska risken för dataintrång och säkerställa att deras korttransaktioner är säkra.
PCI-krav för lagring av kortuppgifter
PCI DSS innehåller krav för företag gällande lagring av kortuppgifter, till exempel:
Begränsa datalagring: Lagra endast de kortuppgifter som är nödvändiga för affärsbehoven. Lagra inte känsliga autentiseringsdata efter auktorisering, även om de är krypterade. Detta inkluderar data som fullständig magnetremsa, kortvalideringskod eller personligt identifieringsnummer (PIN)/PIN-block.
Skydda lagrade data: Kryptera all lagrad data från kortinnehavaren, inklusive PAN, som bör göras oläslig var som helst där den lagras med hjälp av metoder som kryptografi.
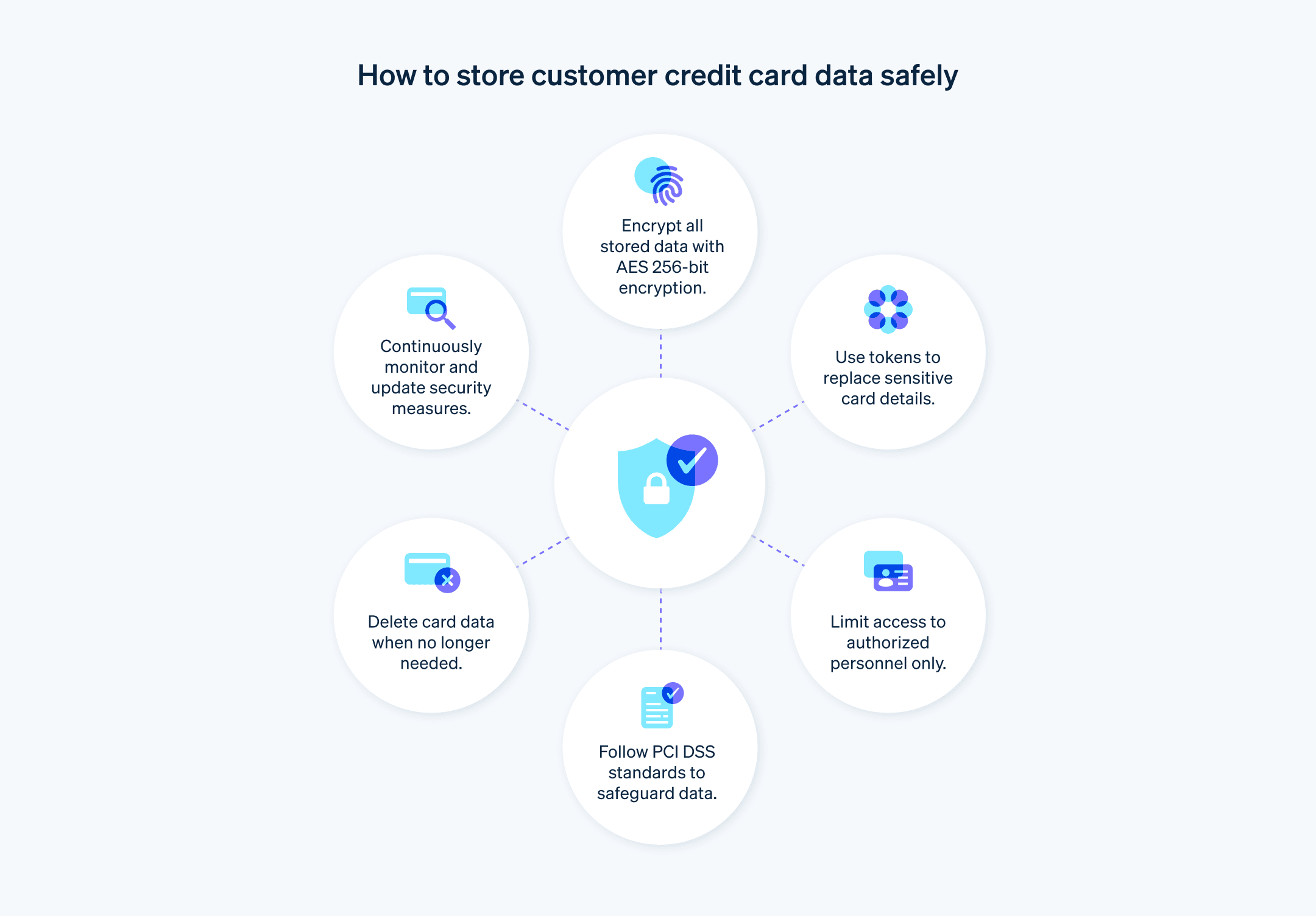
Begränsa dataåtkomst: Åtkomst till kortinnehavarens uppgifter bör begränsas till personer vars arbete kräver det. Implementera en policy som begränsar åtkomsten till de som verkligen behöver den.
Skapa unika ID:n: Tilldela ett unikt ID till varje person med datoråtkomst till kortinnehavarens data. Efter ett dataintrång hjälper detta till att spåra vem som har fått åtkomst till data.
Skydda fysiska platser: Skydda de fysiska platser där kortinnehavarens data lagras. Detta inkluderar åtgärder som övervakning, begränsad åtkomst till datalagringsområden och säkra lagringssystem.
Ange policyer för lagring och radering av data: Utveckla en datalagringspolicy som raderar kortinnehavarens data så snart de inte längre behövs. Ta bort den typen av data och se till att den inte kan återställas.
Använd krypteringsnycklar: Se till att implementera stark kryptografi och säkerhetsprotokoll som Secure Sockets Layer (SSL)/Transport Layer Security (TLS) eller Internet Protocol Security (IPSEC) för att skydda känsliga data från kortinnehavare vid överföring över öppna, offentliga nätverk.
Bästa metoder för lagring av kortuppgifter
Företag kan ta många vägar för att följa PCI-efterlevnadskraven. Följande metoder hjälper företag att skydda sina kunders kortuppgifter och upprätthålla PCI-efterlevnad på ett sätt som skyddar användarupplevelsen:
Minimera lagring av kortinnehavarens data: Spara endast nödvändiga uppgifter om kortinnehavaren och undvik att behålla känsliga data om det inte är absolut nödvändigt. Genom att minska mängden lagrade data kan du minimera riskerna och förenkla efterlevnadsarbetet.
Anta AES (Advanced Encryption Standard): Använd AES med en 256-bitars nyckel för att kryptera lagrad data om kortinnehavaren. Den här metoden är i linje med med nuvarande bästa praxis och överträffar minimikraven för efterlevnad.
Implementera end-to-end-kryptering (E2EE): Utöver grundläggande krypteringsmetoder kan du använda E2EE för att skydda kortinnehavarens data från insamlingstillfället tills den når den säkra behandlingsmiljön.
Förbättra mekanismerna för åtkomstkontroll: Använd multifaktorautentisering och detaljerade rollbaserade åtkomstkontroller för att säkerställa att endast behörig personal kan komma åt känsliga data från kortinnehavaren, med en tydlig verifieringskedja för all åtkomst och vidtagna åtgärder.
Integrera DLP-verktyg: Implementera DLP-strategier för att övervaka och kontrollera dataöverföring, förhindra datastöld och se till att kortinnehavarens data inte lagras eller distribueras felaktigt.
Genomför regelbundna säkerhetstester: För att proaktivt identifiera och åtgärda potentiella säkerhetsbrister bör du utföra sofistikerade penetrationstester och sårbarhetsbedömningar utöver standardkraven enligt PCI DSS.
Överväg att använda avancerade tokeniseringstekniker: Överväg att använda dynamisk tokenisering, där token varierar med varje transaktion, för att ge ett extra lager av säkerhet och ytterligare minska användbarheten av uppfångad data.
Använd automatiserad övervakning av efterlevnad: Använd automatiserade verktyg för att kontinuerligt övervaka efterlevnaden av PCI DSS-standarder och snabbt upptäcka och åtgärda eventuella avvikelser.
Använd en arkitektur med nolltillit: Inför ett säkerhetsramverk med nolltillit som förutsätter att alla användare, även de inom organisationen, potentiellt kan äventyra kortinnehavarens data genom att tillämpa principer för strikt verifiering och mycket begränsad åtkomst.
Utforska kvantresistenta kryptografiverktyg: För att skydda mot nya kvantberäkningshot kan du fundera på att integrera kvantresistenta kryptografiska algoritmer.
Ta fram en åtgärdsplan: Ha en plan för att svara på säkerhetsincidenter. Om ett dataintrång inträffar bör du snabbt kunna identifiera problemet, begränsa intrånget och minska eventuella skador.
Utmaningar och lösningar för lagring av kortuppgifter
Lagring av kortuppgifter är nära knutet till många aspekter av kundupplevelsen, hur produkter och tjänster nås och hur det interna teamet hanterar sin interaktion med kunddata. Även de mest väldesignade kortlagringssystemen är mycket komplexa. Här är några vanliga utmaningar och lösningar:
Skalbarhet
- Utmaning: I takt med att transaktionsvolymerna ökar kan det vara svårt att upprätthålla hög prestanda och PCI-efterlevnad. Skalbarhetsproblem kan påverka kundupplevelsen och den operativa effektiviteten.
- Lösning: Implementera en distribuerad databasarkitektur som kan hantera hög genomströmning av att läsa/skriva och samtidigt upprätthålla datakonsekvens och efterlevnad. Använd elastiska molnbaserade lösningar som kan skalas dynamiskt som svar på fluktuerande efterfrågan och bibehålla prestanda utan att kompromissa med säkerheten.
Föråldrad systemintegration
- Utmaning: Många organisationer använder föråldrade system som inte är utformade för att uppfylla PCI DSS-standarder. Detta kan skapa luckor i efterlevnad och säkerhet.
- Lösning: Använd dataabstraktionslager eller tjänsteinriktade arkitekturer för att kapsla in föråldrade system och minimera den direkta åtkomsten till kortinnehavarens data. Överväg att ersätta eller modernisera föråldrade system över tid med hjälp av mikrotjänster eller containerisering för att förbättra flexibiliteten och efterlevnaden.
Dataintegritet över gränserna
- Utmaning: Olika regioner har olika regler om dataintegritet och efterlevnadskraven ökar för företag när de lagrar kortinnehavares data över gränserna.
- Lösning: Implementera lösningar för datahemvist som bearbetar och lagrar data i enlighet med lokala föreskrifter. Använd geolokaliseringsbaserad datalagring och bearbetning för att automatiskt skicka och lagra data i enlighet med kortinnehavarens plats och i enlighet med regionala efterlevnadskrav.
Avancerade säkerhetshot
- Utmaning: Eftersom angripare ständigt utvecklar nya taktiker måste organisationer kämpa mot allt mer sofistikerade cyberattacker och avancerade ihållande hot som kan kringgå konventionella säkerhetsåtgärder.
- Lösning: Anta en säkerhetsmetod i flera lager som omfattar avancerade mekanismer för att identifiera hot och svara på dem, till exempel AI-driven beteendeanalys för att identifiera och minimera hot i realtid. Uppdatera regelbundet dina planer för incidenthantering och katastrofåterställning för att hantera nya typer av cyberhot.
Förändrade efterlevnadsstandarder
- Utmaning: PCI DSS-standarder och relaterade regulatoriska krav utvecklas ständigt, och att hålla sig kompatibel kan vara en ständig utmaning.
- Lösning: Upprätta ett program för kontinuerlig övervakning av efterlevnad som använder automatiserade verktyg för spårning och rapportering av efterlevnad. Delta i proaktiva branschforum och samarbeten för att ligga steget före nya standarder och införliva bästa praxis i din efterlevnadsstrategi.
Datakvalitet och enhetlighet
- Utmaning: Det kan vara svårt att säkerställa integritet och konsekvens av kortinnehavarens data i en mängd olika system och lagringsmiljöer, särskilt i distribuerade arkitekturer.
- Lösning: Implementera starka ramverk för datastyrning och använd verktyg för hantering av datakvalitet som upprätthåller datanoggrannhet och konsekvens. Använd datasynkronisering och replikering som uppfyller ACID-egenskaperna (atomicitet, konsistens, isolering och varaktighet) för att upprätthålla dataintegriteten.
Så kan Stripe hjälpa dig
Att arbeta med Stripe kan hjälpa företag att minska bördan av PCI DSS-efterlevnad. Genom att behandla betalningar via Stripe hanterar företag inte känsliga kortuppgifter direkt, vilket minskar omfattningen av deras efterlevnadsansvar. Stripe är en certifierad PCI-tjänsteleverantör nivå 1, den högsta nivån av PCI-efterlevnad, och hanterar majoriteten av alla uppgifter gällande datasäkerhet för kort. Dessa funktioner från Stripe skyddar kortinnehavarens data samtidigt som de hjälper företag att efterleva PCI-krav:
Tokenisering: Stripes tokeniseringstjänst ersätter känsliga kortuppgifter med unika identifierare (tokens) som kan lagras säkert och användas för transaktioner utan att exponera kortuppgifter.
E2EE: Stripe krypterar alla känsliga data från det att de samlas in tills de behandlas i företagets säkra miljö. Denna end-to-end-kryptering minimerar risken för att data fångas upp under överföringen.
Skalbarhet: Stripes infrastruktur bygger på en molnplattform som är utformad för att hantera stora transaktionsvolymer utan att kompromissa med prestandan. Företag kan skala upp sin verksamhet utan att behöva oroa sig för att upprätthålla efterlevnads- och säkerhetsstandarder.
Integration med moderna och föråldrade system: Stripe erbjuder omfattande stöd för API (Application Programming Interface), vilket gör det enkelt att integrera med moderna och föråldrade system. Den här flexibiliteten hjälper företag att modernisera sin betalningshantering utan behov av omfattande översyn av befintliga system.
Kontinuerlig övervakning och uppdateringar: Stripe övervakar kontinuerligt sina system för hot och uppdaterar regelbundet sina säkerhetsåtgärder för att hantera nya sårbarheter. Säkerhetsfunktioner inkluderar maskininlärningsalgoritmer som identifierar och förhindrar bedrägerier.
Global efterlevnad: Stripe verkar globalt och kan hjälpa företag att hantera den komplexa situationen med datahemvist och regional efterlevnad över gränserna.
Datastyrning: Stripes infrastruktur stöder dataintegritet och konsekvens.
Genom att förlita sig på att Stripe hanterar huvuddelen av ansvaret för säker kortlagring, datakryptering, efterlevnad och skalbarhet kan företag lägga mer tid på kärnverksamheten. Läs mer om Stripes säkerhetsstandarder.
Innehållet i den här artikeln är endast avsett för allmän information och utbildningsändamål och ska inte tolkas som juridisk eller skatterelaterad rådgivning. Stripe garanterar inte att informationen i artikeln är korrekt, fullständig, adekvat eller aktuell. Du bör söka råd från en kompetent advokat eller revisor som är licensierad att praktisera i din jurisdiktion för råd om din specifika situation.