How Stripe responded to a wave of card testing attacks
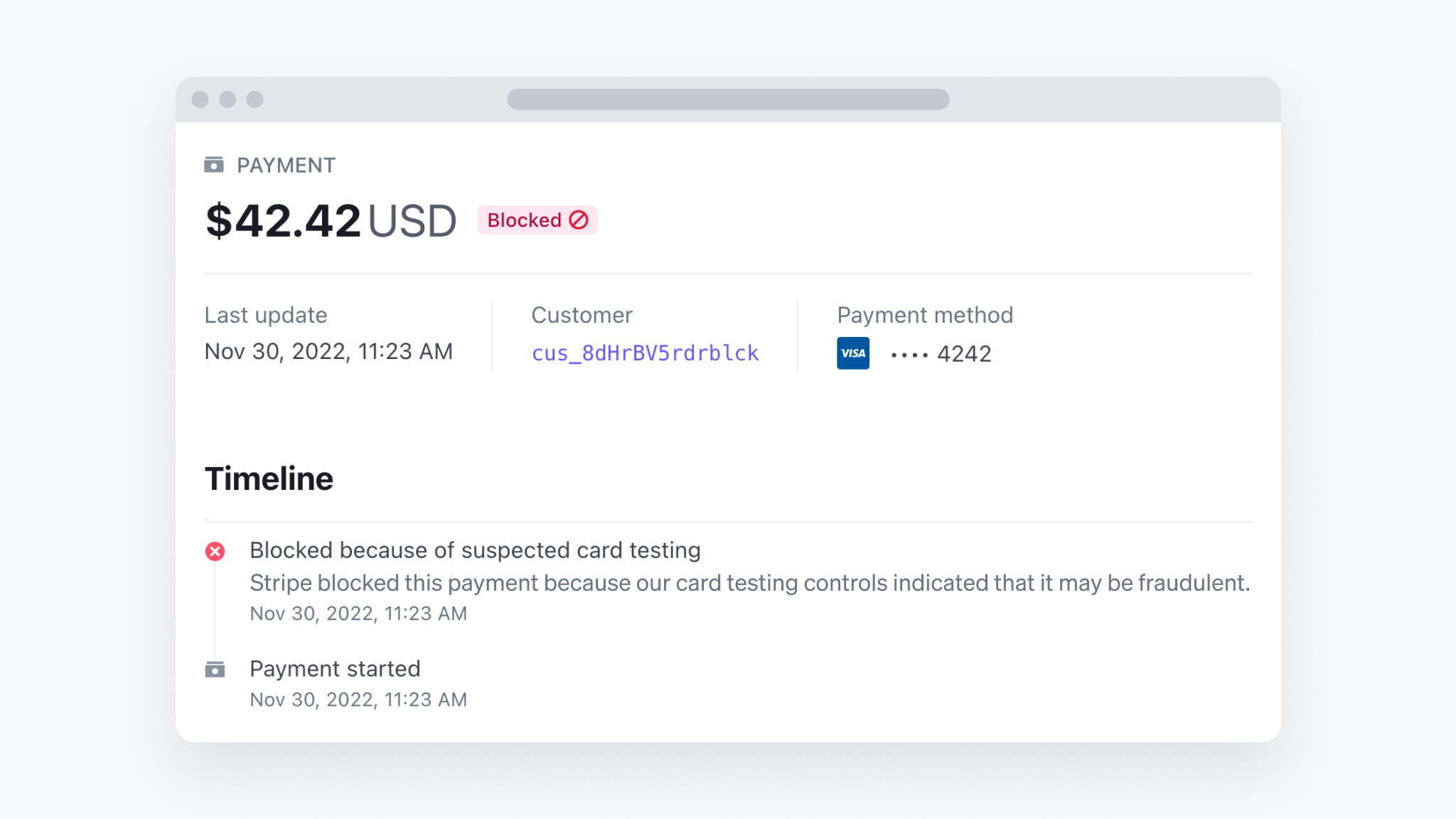
Between February and August 2022, Stripe tracked a surge of credit card fraud in which bad actors inundated merchants with millions of small- or zero-dollar transactions. These “card testing” attacks allow criminals to verify that stolen credit cards still work and can cripple businesses. At the peak of the wave, Stripe Radar—Stripe’s fraud prevention solution—blocked more than 20 million card testing attempts per day.
The summer wave was part of a trend. Card testing has accelerated over the last few years as more businesses have moved online. Many are unfamiliar with the intricacies of ecommerce and have left themselves vulnerable to bad actors. Card testing attempts have spiked as a result—up more than 100x since 2019.

Verifying stolen cards
Card testing plays a crucial role in the process bad actors use to extract value from stolen credit card details. When they purchase a list of credit card details, they don’t know which cards are still active. Some might have been canceled and others might have expired. This makes it hard to know the real value of the list.
This is where card testing comes in.
Card testers create programs that automatically attempt to make a small payment with each card in a set, or to save it on a site as a validated payment source. Cards that are used or saved successfully can be sold to other bad actors who can use them to make larger purchases or manufacture counterfeit cards.
“Fraud in general is an ecosystem where you have different players that are doing different things in the value chain in order to ultimately make money,” said Will Megson, product lead for Radar.
Harming merchants
Mass card testing is a problem for vendors and platforms aside from its role in abetting fraud. Vendors pay network fees for each transaction. These are small on a per transaction basis, but add up when a site is suddenly used for thousands or even millions of card tests. Small merchants can go bankrupt due to card testing in just a few hours.
And that’s just the start. Even small card testing charges may be disputed by a cardholder, resulting in chargebacks which carry a host of costs for merchants: dispute fees, resolution fees, interchange fees, plus hours of work resolving it all. As a result, card networks can place merchants in high-risk categories, such as the Visa Fraud Monitoring Program or the Mastercard Excessive Fraud Merchant Compliance Program, which come with increased processing fees and merchant reserves.
“While these programs offer protective controls, they can be punitive,” said Megson.
Radar responds
The good news is that businesses can fight back with little effort on their part—Radar does the work for them.
In response to the card testing surge, Stripe engineers streamlined the flow of data from the Stripe network into Radar. This made it possible to launch upgraded models within an hour—accelerating a process that previously took a day or two and allowing Radar to adapt to fast-moving fraud trends.
“By leveraging Stripe’s machine learning and custom fraud rules, we've seen a decrease in our fraud rates and chargeback rates,” said Lourdes García, product manager at the online optical store Ben & Frank.
Stripe also built a new transaction-level card testing machine learning model. Doing so required developing new methods for accurately labeling card testing transactions, beyond the existing state of the art—a previously prohibitive step because card networks don’t provide card testing labels of any kind.
In addition to these machine learning improvements, Stripe introduced dozens of new rate limiters, which cap the number of requests the Stripe API will process in a short period of time. This step alone has blocked nearly 40 million card testing transactions this year.
“We’re getting much smarter about monitoring how card testing scripts interact with merchants,” said Megson.
Blocking more attacks
The results have been encouraging. So far this year, Radar has blocked an additional 400 million fraudulent transactions, cutting the number of card testing attacks that slip through in half—without increasing the rate at which legitimate transactions are misidentified as fraud.
“We were on the cusp of losing the ability to process payments due to the number of fraudulent transactions. That’s when we started using Radar, which allowed us to programmatically fight fraud and institute fine-grained ways to fight back against card testers,” said Matt Maier, CEO of AdBlock.
Stripe continues to invest in Radar by combining innovations in machine learning with real-world lessons from the fight against card testing. As card testing evolves, Radar will, too.